

Back
In the era of global digitization and increasing scale of hacking attacks, password-based authentication is exposed to numerous threats. Therefore, it is crucial to adopt alternative authentication methods that are both secure and practical, while also being convenient for users. One of these methods is passwordless authentication.
Passwords are the most common form of authentication and are practically used in all IT-related domains. They offer an incredibly versatile solution - they can be applied to nearly everything requiring authentication, from accessing devices, documents, accounts, and services to various smartphone applications. With few exceptions, nearly every application or service involves passwords. Passwords are easily managed, simple to implement, and do not necessitate significant infrastructure.
It might seem that passwords are user secrets, known only to them, but in reality, they are also exposed to the services or software used. Consequently, passwords are stored on various devices and can be shared or disclosed. This implies that passwords do not provide full security and can be compromised or stolen. Best practices such as using unique and complex passwords, avoiding their recording or sharing, are often insufficient. Even a strong password can be vulnerable to hacking attacks like phishing or brute force.
Phishing is a form of cyber attack where an individual or organization impersonates a trusted entity to deceive users (e.g., online) into revealing sensitive information like passwords, credit card numbers, or personal data. Common forms of phishing include fake emails, text messages, social media messages, fake websites, and advertisements. Criminals send authentic-looking messages, enticing users to click on manipulated links or urging them to download suspicious files, leading to computer infections or data theft.
Phishing currently stands as one of the most prevalent methods for targeting online users and poses a serious threat to information security. To minimize the risk of phishing attacks, users should exercise caution with suspicious email messages, avoid sharing sensitive information without confirming the message's authenticity, and employ antivirus and antimalware software to shield their computers from malicious software.
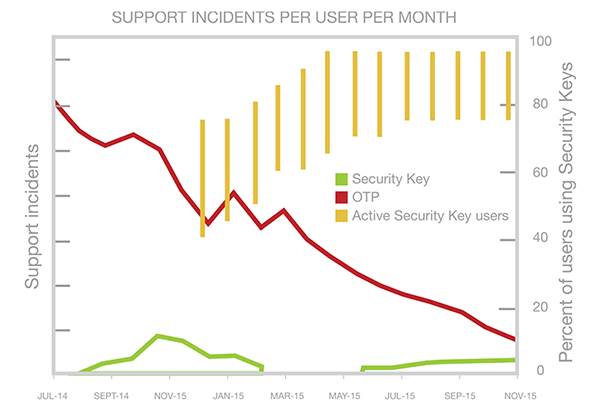
Brute force is another method of computer attack involving trying all possible combinations of passwords, encryption keys, or other parameters until the correct value is found. While time-consuming and resource-intensive, brute force attacks can be effective if the attacker possesses sufficient computational resources and time to test all possible combinations.
Faced with these threats, alternative authentication methods that do not rely on passwords have become increasingly significant, primarily for their effectiveness. Passwordless authentication has become one of the foremost challenges in the digital realm. Companies and institutions are increasingly embracing these alternative methods to enhance security and user convenience.
Yubico, a leader in the market of passwordless authentication solutions, offers devices based on the FIDO standard, supported by numerous major companies. Yubico devices use NFC or USB technology, enabling secure authentication on computers, tablets, and smartphones.
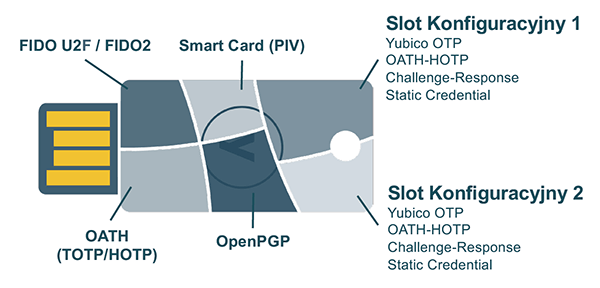
One of Yubico's most popular products is the YubiKey. This small device connects to a USB port or employs NFC technology for secure authentication. YubiKey operates based on the FIDO U2F standard, requiring the physical presence of the key for user login. Even if a hacker gains access to the password, they cannot enter without the physical key. Another option is YubiKey with OTP technology, generating one-time authentication codes. Users input this code during login, enhancing security and impeding hackers from taking over accounts. Yubico also provides various other passwordless authentication options.
The Yubico team operates in 11 countries, but YubiKey security keys are manufactured exclusively in Sweden and the USA, a crucial factor in the current international climate.
IMPORTANT: One key offers multiple possibilities and can be used in various ways. Yubico (depending on the model) supports the following authentication protocols:
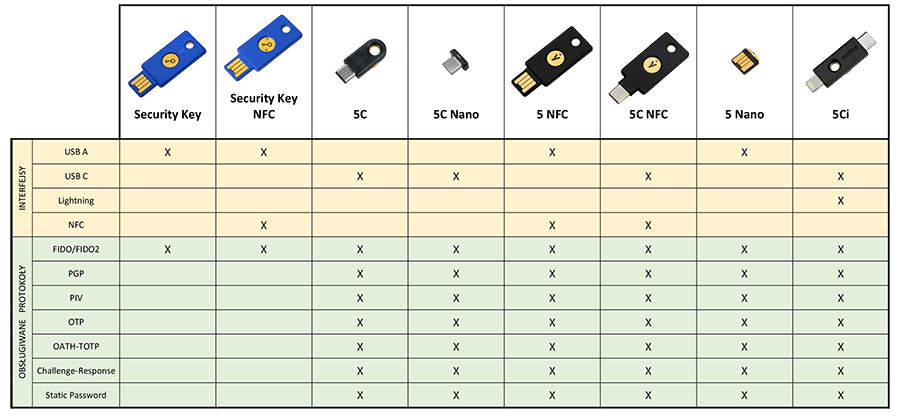
Depending on security needs and considerations, various YubiKey options can be employed, ranging from those with built-in fingerprint readers to different USB options and NFC support.
Therefore, passwordless authentication significantly enhances the level of cybersecurity for companies, institutions, and private users. As a Yubico partner, KOMA NORD offers comprehensive services for implementing this technology in various organizations.
Free Research Preview. ChatGPT may produce inaccurate information about people, places, or facts. ChatGPT August 3 Version
|
Secretary: +48 58 621 11 00 Mobile: +48 605 126 099 Fax: +48 58 621 10 30
|
|
E-mail:
|


